- i18n (de Lille1)
- correctif pour la recherche des noms de groupe [1]
- remplacement de la recherche des personnes par le webwidget https://github.com/prigaux/wsgroups (voir aussi http://wsgroups.univ-paris1.fr/web-widget/test-search-user.html ) pour contourner l'absence de gestion des homonymes. Cf patches et README_univ_modification.md
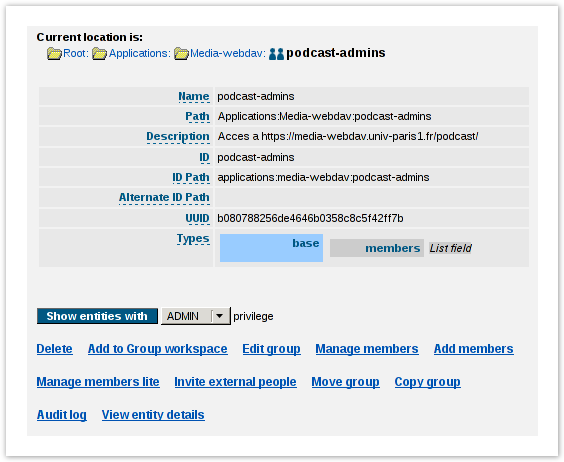
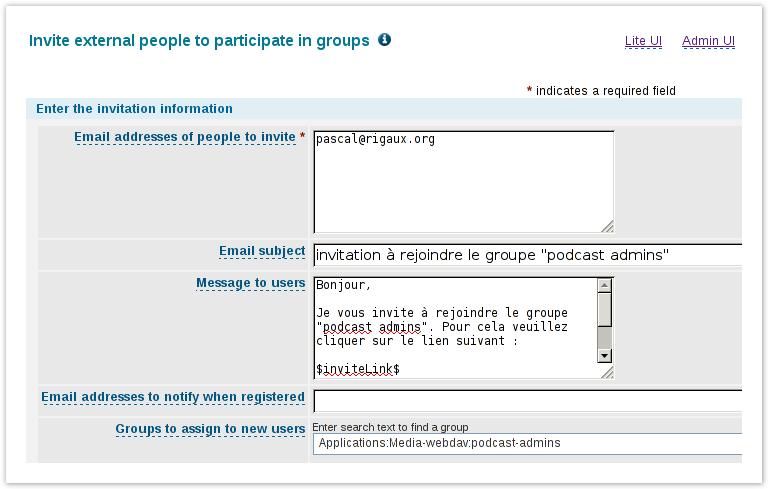
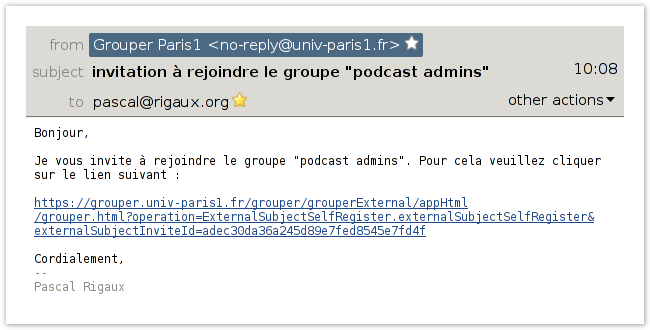
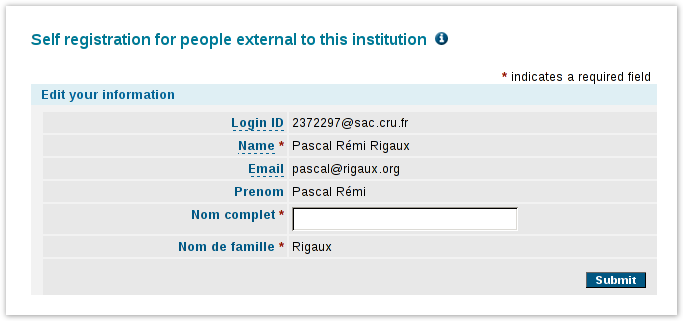
- intégration dans l'ENT, avec :
- suppression de la colonne de gauche pour simplifier l'interface
- mise en valeur du bouton "+ Ajouter des membres"
- psp pour synchroniser grouper vers OpenLDAP
- avec gestion supannGroupeAdminDn et supannGroupeLecteurDn
avec gestion businessCategory, seeAlso, labeledURI (pour les groupes crées automatiquement par GSHcreator.py)
suite à des pbs avec la synchro incrémentale PspChangeLogConsumer [2] toutes les 10 secondes, remplacement par un petit script plus puissant [3] appelant :gsh -psp -sync <noms de groupes mentionnés dans la table grouper_change_log_type>
- des groupes de bases de données variées vers grouper (apogee, sof, sifac, sesame, harpege)
- des groupes de LDAP vers grouper (groupes créés automatiquement avec le script : https://subversion.cru.fr/esup-tools/PAGScreator/trunk/GSHcreator.py )